| The Following User Says Thank You to StefanL For This Useful Post: | ||
|
|
2012-03-02
, 12:50
|
|
|
Posts: 5,028 |
Thanked: 8,613 times |
Joined on Mar 2011
|
#1182
|
You're correct, but obviously, AP name appears only, if there was a client connected, and it re-connect after re-auth. There is also problem of correct read timing (AP name is broadcast only for short moment) - I have no idea how to implement it properly, but it can't be too hard, as desktop/notebook tools seems to have 100% "success rate".
Easiest way for de-auth would be to use broadcast one (targeting AP, not clients), but it may not work for all AP's/clients. Other way is to target clients using same channel and BSSID (AP's MAC), which should be working 99,99% of times.
Also, maybe it's possible to use fake authentication to reveal hidden AP SSID- in this case, no clients connected would be needed (yet, one would still need to known authorized MAC, in case of MAC filtering).
/Estel
Easiest way for de-auth would be to use broadcast one (targeting AP, not clients), but it may not work for all AP's/clients. Other way is to target clients using same channel and BSSID (AP's MAC), which should be working 99,99% of times.
Also, maybe it's possible to use fake authentication to reveal hidden AP SSID- in this case, no clients connected would be needed (yet, one would still need to known authorized MAC, in case of MAC filtering).
/Estel
__________________
N900's aluminum backcover / body replacement
-
N900's HDMI-Out
-
Camera cover MOD
-
Measure battery's real capacity on-device
-
TrueCrypt 7.1 | ereswap | bnf
-
Hardware's mods research is costly. To support my work, please consider donating. Thank You!
N900's aluminum backcover / body replacement
-
N900's HDMI-Out
-
Camera cover MOD
-
Measure battery's real capacity on-device
-
TrueCrypt 7.1 | ereswap | bnf
-
Hardware's mods research is costly. To support my work, please consider donating. Thank You!
|
|
2012-03-02
, 13:04
|
|
Posts: 105 |
Thanked: 87 times |
Joined on Jun 2011
@ Unknown
|
#1183
|
Originally Posted by Estel


You're correct, but obviously, AP name appears only, if there was a client connected, and it re-connect after re-auth. There is also problem of correct read timing (AP name is broadcast only for short moment) - I have no idea how to implement it properly, but it can't be too hard, as desktop/notebook tools seems to have 100% "success rate".
Easiest way for de-auth would be to use broadcast one (targeting AP, not clients), but it may not work for all AP's/clients. Other way is to target clients using same channel and BSSID (AP's MAC), which should be working 99,99% of times.
Also, maybe it's possible to use fake authentication to reveal hidden AP SSID- in this case, no clients connected would be needed (yet, one would still need to known authorized MAC, in case of MAC filtering).
/Estel
at the moment I am using kismet to reveal the hidden aps name I beleve is using aircrack-ng (not to sure as I am not an expert and still learning pentest) as a silent listening to the aps broadcast to reveal name.
| The Following User Says Thank You to g0r For This Useful Post: | ||
|
|
2012-03-04
, 23:26
|
|
|
Posts: 84 |
Thanked: 22 times |
Joined on Nov 2011
@ Italy
|
#1184
|
Originally Posted by StefanL

Ok... here you go: I launched it from the gear, and, when I click on "Packet Capture", in the window where are shown the networks, there are found networks, and about my router, it just says:
Just run it from the editor using the icon on the right looking like a gear.
PS: You have now made the first step on becoming an ace developer on the N900.
essid = TP-LINK CA 1.2\
More than a developer, I think I'm a very efficient tester!


__________________
I'm Winston Wolf, I solve problems
I'm Winston Wolf, I solve problems
| The Following User Says Thank You to Mr Wolf For This Useful Post: | ||
|
|
2012-03-07
, 21:34
|
|
|
Posts: 298 |
Thanked: 341 times |
Joined on Aug 2010
@ This world :)
|
#1185
|
Fixed version 0.49 has been posted to original post. Check the signature to get there.
__________________
My phone evolution: Nokia 7610 (RIP), N82 (RIP), BB9000 (RIP), N900, BB9760 (RIP), N8, BB9900, N9 64GB
Working : Python Gorillas (Maemo5)
: Python Gorillas (Maemo5)  Faircrack0.50 Update (Maemo5)
Faircrack0.50 Update (Maemo5) 
Not so much : WPScrack (Maemo5)
: WPScrack (Maemo5)
My phone evolution: Nokia 7610 (RIP), N82 (RIP), BB9000 (RIP), N900, BB9760 (RIP), N8, BB9900, N9 64GB
Working
 : Python Gorillas (Maemo5)
: Python Gorillas (Maemo5)  Faircrack0.50 Update (Maemo5)
Faircrack0.50 Update (Maemo5) 
Not so much
 : WPScrack (Maemo5)
: WPScrack (Maemo5)
|
|
2012-03-11
, 12:08
|
|
|
Posts: 84 |
Thanked: 22 times |
Joined on Nov 2011
@ Italy
|
#1186
|
Hi! I've just tried, and I have the same problem as above. 
EDIT: I've just switched back to 0.48 and have the same problem.
Maybe I should try a clean install.
EDIT: I deleted the FAS folder, re-extracted 0.3, then 0.49 and have the same problem.
Last edited by Mr Wolf; 2012-03-11 at 14:15.

EDIT: I've just switched back to 0.48 and have the same problem.

Maybe I should try a clean install.

EDIT: I deleted the FAS folder, re-extracted 0.3, then 0.49 and have the same problem.
__________________
I'm Winston Wolf, I solve problems
I'm Winston Wolf, I solve problems
Last edited by Mr Wolf; 2012-03-11 at 14:15.
| The Following User Says Thank You to Mr Wolf For This Useful Post: | ||
|
|
2012-03-29
, 15:54
|
|
|
Posts: 298 |
Thanked: 341 times |
Joined on Aug 2010
@ This world :)
|
#1187
|
Quick note on using fAircrack V0.49 with KP 50:
As per Estel's post, all you need to do is copy all the .ko files from the v0.2 drivers to ~/MyDocs/wl1251-maemo/binary/compat-wireless directory and just ignore the warning produced by fAircrack on the Monitor Tab. I have a working V0.50 (to match KP50 ), but I promised Estel to push out V0.50 via repositories, and I am not ready yet
), but I promised Estel to push out V0.50 via repositories, and I am not ready yet  .
.
So, for all our noobs out there (assuming you already had a fully working fAircrack V0.49 or earlier for KP49 or earlier version on you N900):
1. Download the driver for KP50 as per pali's post. Thank the author for still supporting our device .
.
2. Extract in the directory the file was downloaded to
3. Change to the compat-wireless subdirectory
4. Copy all *.ko files to the correct directory
Hint: Only need to type the first few letters of a directory or filename and then use the Tab button on the X Terminal screen to complete the rest of the word.
Have fun
As per Estel's post, all you need to do is copy all the .ko files from the v0.2 drivers to ~/MyDocs/wl1251-maemo/binary/compat-wireless directory and just ignore the warning produced by fAircrack on the Monitor Tab. I have a working V0.50 (to match KP50
 ), but I promised Estel to push out V0.50 via repositories, and I am not ready yet
), but I promised Estel to push out V0.50 via repositories, and I am not ready yet  .
.So, for all our noobs out there (assuming you already had a fully working fAircrack V0.49 or earlier for KP49 or earlier version on you N900):
1. Download the driver for KP50 as per pali's post. Thank the author for still supporting our device
 .
.2. Extract in the directory the file was downloaded to
Code:
tar -xzvf wl1251-maemo-0.2-power49+pre50.tar.gz
Code:
cd wl1251-maemo/binary/compat-wireless
Code:
cp *.ko ~/MyDocs/wl1251-maemo/binary/compat-wireless
Have fun

__________________
My phone evolution: Nokia 7610 (RIP), N82 (RIP), BB9000 (RIP), N900, BB9760 (RIP), N8, BB9900, N9 64GB
Working : Python Gorillas (Maemo5)
: Python Gorillas (Maemo5)  Faircrack0.50 Update (Maemo5)
Faircrack0.50 Update (Maemo5) 
Not so much : WPScrack (Maemo5)
: WPScrack (Maemo5)
My phone evolution: Nokia 7610 (RIP), N82 (RIP), BB9000 (RIP), N900, BB9760 (RIP), N8, BB9900, N9 64GB
Working
 : Python Gorillas (Maemo5)
: Python Gorillas (Maemo5)  Faircrack0.50 Update (Maemo5)
Faircrack0.50 Update (Maemo5) 
Not so much
 : WPScrack (Maemo5)
: WPScrack (Maemo5)
| The Following 5 Users Say Thank You to StefanL For This Useful Post: | ||
|
|
2012-03-30
, 11:15
|
|
|
Posts: 298 |
Thanked: 341 times |
Joined on Aug 2010
@ This world :)
|
#1188
|
Originally Posted by Mr Wolf

Confirmed, I am still having an issue with the revised character handling I introduced in V0.48. Should be fixed in next v.50, due out when I get a handle on the repository thingy 
Hi! I've just tried, and I have the same problem as above.
EDIT: I've just switched back to 0.48 and have the same problem.
Maybe I should try a clean install.
EDIT: I deleted the FAS folder, re-extracted 0.3, then 0.49 and have the same problem.
 . Might have to roll-back to V0.47 character handling code.
. Might have to roll-back to V0.47 character handling code.
__________________
My phone evolution: Nokia 7610 (RIP), N82 (RIP), BB9000 (RIP), N900, BB9760 (RIP), N8, BB9900, N9 64GB
Working : Python Gorillas (Maemo5)
: Python Gorillas (Maemo5)  Faircrack0.50 Update (Maemo5)
Faircrack0.50 Update (Maemo5) 
Not so much : WPScrack (Maemo5)
: WPScrack (Maemo5)
My phone evolution: Nokia 7610 (RIP), N82 (RIP), BB9000 (RIP), N900, BB9760 (RIP), N8, BB9900, N9 64GB
Working
 : Python Gorillas (Maemo5)
: Python Gorillas (Maemo5)  Faircrack0.50 Update (Maemo5)
Faircrack0.50 Update (Maemo5) 
Not so much
 : WPScrack (Maemo5)
: WPScrack (Maemo5)
|
|
2012-05-16
, 22:34
|
|
|
Posts: 84 |
Thanked: 22 times |
Joined on Nov 2011
@ Italy
|
#1189
|
Hi! I was using fAircrack and noticed a thing: sometimes, when I use Korek attack (aircrack-ng -K), it doesn't work, it stays cracking the key forever, while PTW attack (aircrack-ng -z) works; other times, it's just the contrary.
My knowledgment, in this case, is not so great to understand why, so, I guess you have just to try both methods.
to understand why, so, I guess you have just to try both methods.
Then, why when a network is hidden, it shows weird channel numbers?
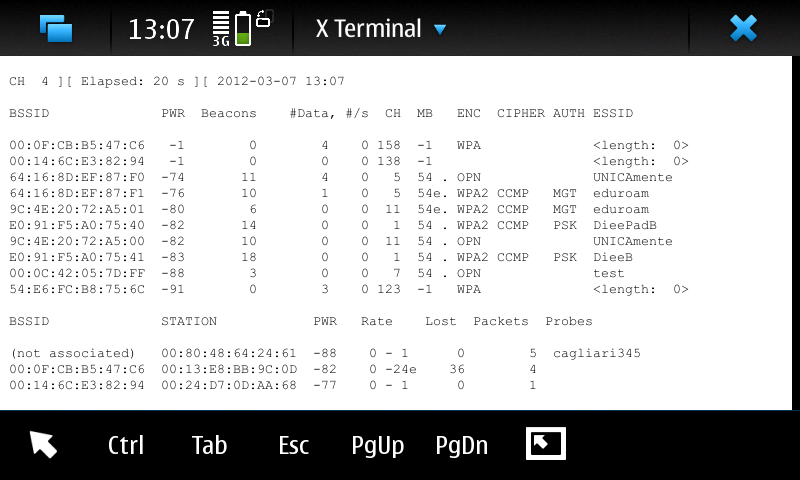
This way, it's not possible to use deauthentication attack to find network ESSID.
My knowledgment, in this case, is not so great
 to understand why, so, I guess you have just to try both methods.
to understand why, so, I guess you have just to try both methods.Then, why when a network is hidden, it shows weird channel numbers?

This way, it's not possible to use deauthentication attack to find network ESSID.
__________________
I'm Winston Wolf, I solve problems
I'm Winston Wolf, I solve problems
|
|
2012-05-17
, 04:40
|
|
Posts: 2 |
Thanked: 0 times |
Joined on Jan 2012
|
#1190
|
Originally Posted by StefanL

hello
1. Download the driver for KP50 as per pali's post. Thank the author for still supporting our device.
2. Extract in the directory the file was downloaded to3. Change to the compat-wireless subdirectoryCode:tar -xzvf wl1251-maemo-0.2-power49+pre50.tar.gz4. Copy all *.ko files to the correct directoryCode:cd wl1251-maemo/binary/compat-wirelessHint: Only need to type the first few letters of a directory or filename and then use the Tab button on the X Terminal screen to complete the rest of the word.Code:cp *.ko ~/MyDocs/wl1251-maemo/binary/compat-wireless
Have fun
the second file (source 450mb) must be extract in the directory too???
sorry but i'm rookie. Thanx
 |
| Tags |
| aircrack, aircrack-ng, epicfacepalm, pen testing, rtfm dude! |
«
Previous Thread
|
Next Thread
»
|
All times are GMT. The time now is 11:40.









My phone evolution: Nokia 7610 (RIP), N82 (RIP), BB9000 (RIP), N900, BB9760 (RIP), N8, BB9900, N9 64GB
Working
Not so much