| The Following User Says Thank You to momcilo For This Useful Post: | ||
|
|
2011-09-13
, 09:50
|
|
|
Posts: 2,355 |
Thanked: 5,249 times |
Joined on Jan 2009
@ Barcelona
|
#12
|
Posting the full file is probably not Ok, but I posted the interesting fragment here
Therefore, the only source of nuisance for a free software developer is what is allowed for unsigned applications. So far, even disabling Aegis itself is allowed. But let's see what they have in store.
Last edited by javispedro; 2011-09-13 at 09:57.
Originally Posted by momcilo

That would only work if we were able to sign our own applications -- we are all assuming we are not going to (unless you planned to target Ovi). They do not have any way to identify an unsigned application exclusively, so they can't do that.
So far I've got the feeling that this would allow Nokia (or third party such as ISP) to deny access to certain applications at later time.
Therefore, the only source of nuisance for a free software developer is what is allowed for unsigned applications. So far, even disabling Aegis itself is allowed. But let's see what they have in store.
Last edited by javispedro; 2011-09-13 at 09:57.
|
|
2011-09-13
, 09:53
|
|
Posts: 673 |
Thanked: 856 times |
Joined on Mar 2006
|
#13
|
Originally Posted by javispedro

If you refer to http://pastebin.com/KPX88Sgh, that is unavailable.

Posting the full file is probably not Ok, but I posted the interesting fragment here3
That would only work if we were able to sign our own applications -- we are all assuming we are not going to (unless you planned to target Ovi). They do not have any way to identify an unsigned application exclusively, so they can't do that.
__________________
http://gpl-violations.org/faq/violation-faq.html
http://gpl-violations.org/faq/violation-faq.html
| The Following User Says Thank You to momcilo For This Useful Post: | ||
|
|
2011-09-13
, 09:55
|
|
|
Posts: 2,355 |
Thanked: 5,249 times |
Joined on Jan 2009
@ Barcelona
|
#14
|
Originally Posted by momcilo

Aw, you'll have to wait until tonight then. But that's not that important, it's just a list of tokens and most probably you'll have no idea what they mean unless you're familiar with Harmattan.

If you refer to http://pastebin.com/KPX88Sgh, that is unavailable.
|
|
2011-09-14
, 08:12
|
|
Posts: 673 |
Thanked: 856 times |
Joined on Mar 2006
|
#15
|
Originally Posted by javispedro

The more I read about Harmattan and Mobile Simplified Security Framework, the less I like it.
Aw, you'll have to wait until tonight then. But that's not that important, it's just a list of tokens and most probably you'll have no idea what they mean unless you're familiar with Harmattan.
So far I have confirmed that it is true TPM platform, and it seems to be similar to what Motorola did in past.
__________________
http://gpl-violations.org/faq/violation-faq.html
http://gpl-violations.org/faq/violation-faq.html
| The Following User Says Thank You to momcilo For This Useful Post: | ||
|
|
2011-09-14
, 09:32
|
|
Posts: 673 |
Thanked: 856 times |
Joined on Mar 2006
|
#16
|
I've found the most comprehensive overview of goals and security features of MSSF at:
Mobile Simplified Security Framework MSSFv2, by Dmitry Kasatkin, MeeGo Computers, Nokia, at MeeGo Conf, Moscow, Russia, 11.03.2011
Security goals:
Protection of the user
1.1 Disallow loss/stealing of owner's personal data
2.1 Must meet regulatory requirements and specification
Protection of the Business
3.1 Disallow braking of the SIM/Subsidy Lock
4.1 Allow services such as Music store or App Store and support copy protection
Mobile Simplified Security Framework MSSFv2, by Dmitry Kasatkin, MeeGo Computers, Nokia, at MeeGo Conf, Moscow, Russia, 11.03.2011
Security goals:
Protection of the user
1.1 Disallow loss/stealing of owner's personal data
• E.g mallware sending user's contacts1.2. Miss-use of the device (unexpected costs)
• E.g mallware sending sms to pay numbersProtection of the Device
2.1 Must meet regulatory requirements and specification
• Identity protection2.2 Disallow changing of RF, EM or WiFi tuning values
Protection of the Business
3.1 Disallow braking of the SIM/Subsidy Lock
• Lose of business3.2 Limit what can be installed on the device
• AT&T variant needs to stay AT&T variant3.4 To reduce fraud against Business
• False service bills, Device cloning, back-door manufacturingEnable new services
4.1 Allow services such as Music store or App Store and support copy protection
• Mobile payments and Billing
__________________
http://gpl-violations.org/faq/violation-faq.html
http://gpl-violations.org/faq/violation-faq.html
| The Following 13 Users Say Thank You to momcilo For This Useful Post: | ||
|
|
2011-09-14
, 10:13
|
|
|
Posts: 2,142 |
Thanked: 2,054 times |
Joined on Dec 2006
@ Sicily
|
#17
|
Thank you very much but I don't want this sort of thing.
__________________
Ernesto de Bernardis
Ernesto de Bernardis
|
|
2011-09-14
, 12:00
|
|
|
Posts: 4,672 |
Thanked: 5,455 times |
Joined on Jul 2008
@ Springfield, MA, USA
|
#18
|
TC is controversial because it is technically possible not just to secure the hardware for its owner, but also to secure against its owner. Such controversy has led opponents of trusted computing, such as Richard Stallman, to refer to it instead as treacherous computing, and some academic opponents have begun to place quotation marks around "trusted computing" in scholarly texts.[2][3]
The trusted computing platform need not be used to secure the system against the owner. It is possible to leave to the owner rights of authorization and have no centralized authority. It is also possible to build open source stack of trusted modules, leaving for the security chip only the task to guard against unauthorized modifications. Open source Linux drivers exist [4] to access and use the trusted computing chip. However, uncooperative operating systems can misuse security features to prevent legitimate data exchange.
Source: http://en.wikipedia.org/wiki/Trusted_Computing
The trusted computing platform need not be used to secure the system against the owner. It is possible to leave to the owner rights of authorization and have no centralized authority. It is also possible to build open source stack of trusted modules, leaving for the security chip only the task to guard against unauthorized modifications. Open source Linux drivers exist [4] to access and use the trusted computing chip. However, uncooperative operating systems can misuse security features to prevent legitimate data exchange.
Source: http://en.wikipedia.org/wiki/Trusted_Computing
__________________
Nokia's slogan shouldn't be the pedo-palmgrabbing image with the slogan, "Connecting People"... It should be one hand open pleadingly with another hand giving the middle finger and the more apt slogan, "Potential Unrealized." --DR
Nokia's slogan shouldn't be the pedo-palmgrabbing image with the slogan, "Connecting People"... It should be one hand open pleadingly with another hand giving the middle finger and the more apt slogan, "Potential Unrealized." --DR
| The Following 4 Users Say Thank You to danramos For This Useful Post: | ||
|
|
2011-09-14
, 13:34
|
|
|
Posts: 387 |
Thanked: 566 times |
Joined on Dec 2009
@ Dublin
|
#19
|
Seems like it's more like the current mobile OS's out there. The price to pay for the Service providers to accept it considering how the n900 was easily unlocked from restrictions for example by vodafone. Will wait and see how this develops.
__________________
Never argue with stupid people.They lower you to their level then beat you with experience.
Humility is something we should all taste.
Never argue with stupid people.They lower you to their level then beat you with experience.
Humility is something we should all taste.
| The Following User Says Thank You to smegheadz For This Useful Post: | ||
|
|
2011-09-14
, 14:14
|
|
Posts: 673 |
Thanked: 856 times |
Joined on Mar 2006
|
#20
|
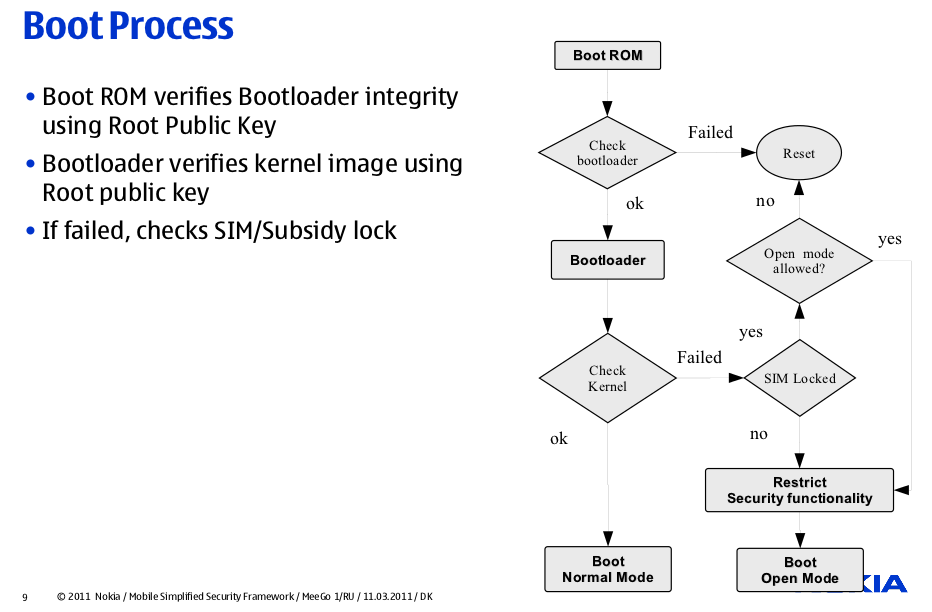
Originally Posted by smegheadz

Based on this diagram it looks like the Service provider can completely disable Open Mode (developer mode, which is restricted btw). I think people should be aware of this before buying this phone. 
Seems like it's more like the current mobile OS's out there. The price to pay for the Service providers to accept it considering how the n900 was easily unlocked from restrictions for example by vodafone. Will wait and see how this develops.
__________________
http://gpl-violations.org/faq/violation-faq.html
http://gpl-violations.org/faq/violation-faq.html
Last edited by momcilo; 2011-09-14 at 14:23.
 |
| Tags |
| locked boot, neutered, trecherous |
«
Previous Thread
|
Next Thread
»
|
All times are GMT. The time now is 10:21.










So far I've got the feeling that this would allow Nokia (or third party such as ISP) to deny access to certain applications at later time.
That would be so Apple-like.
http://gpl-violations.org/faq/violation-faq.html
Last edited by momcilo; 2011-09-13 at 13:34.